In a world of rapidly evolving technologies, information system security is becoming one of the top priorities for organizations.
Hacker attacks, data leaks and other threats require businesses to take effective measures to protect their resources and confidential information. One of the important security tools is Penetration Testing Service Provider, which we will discuss in detail in this article.
What is a pentest?
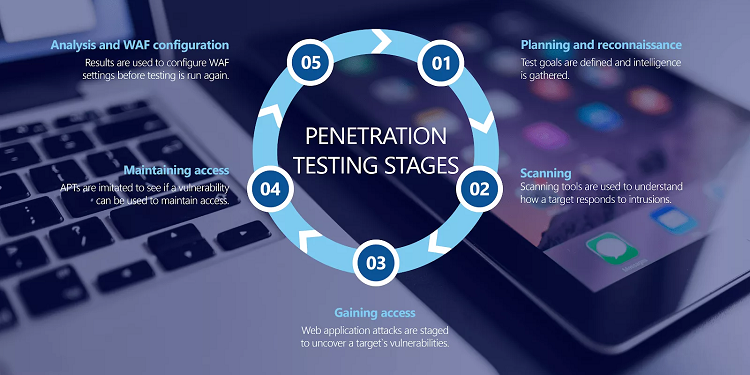
Pen test is a method of checking the security of information systems, networks, applications and other aspects of an organization’s IT infrastructure. This is a controlled process in which security professionals simulate the actions of a potential attacker to identify vulnerabilities.
Penetration Testing allows you to prevent unauthorized access to data, protect infrastructures from attacks and minimize business risks. Conducting a pentest helps identify security weaknesses and eliminate them before attackers exploit them to attack.
Types of pentests
There are several types of pentests, each of which is focused on checking certain aspects of security:
- external – aimed at assessing the security of external resources, such as websites, servers, network devices;
- internal – focuses on analyzing the security of the organization’s internal resources and networks. Conducted internally to identify vulnerabilities that employees can access;
- pentest of web applications – aimed at checking the security of web applications, analyzing them for possible vulnerabilities, such as SQL injections, cross-site scripting and others;
- social – assesses the level of security in the context of social engineering. This type of testing allows you to determine how well the organization’s employees are informed about security rules and whether they are prepared for possible attacks.
Penetration Testing Service Provider offers a full range of services in this area and allows you to order penetration testing of any type.
Pentesting has a number of clear advantages that make it an integral tool for ensuring business security. This process allows us to identify weaknesses in the protection of information systems and take timely measures to eliminate them. Thanks to pentests, you can prevent possible attacks and reduce financial and reputational losses that may arise due to data leaks.